A renowned market leader in exceptional password management, secrets management, privileged access, secure remote access, and encrypted messaging report was published today.
The Keeper Password Management Report: Unifying Perception with Reality, conducted by Keeper Security.
The report examined the password habits of over 8,000 people and found that 3 out of 4 (75%) people worldwide don't follow generally accepted password best practises. The majority (64%) either use weak passwords or frequently changing passwords to secure their online accounts. In addition, more than a third of respondents said they felt overwhelmed when it came to taking steps to increase their cybersecurity, which may be increasing vulnerability to hacking.
According to Darren Guccione, CEO and Co-Founder of Keeper Security, "we asked which animal they would identify with in regard to their cybersecurity behaviours in order to analyse people's personal cybersecurity hygiene." "The industry clearly still has much work to do to get more people comfortable with cybersecurity and better protected as a result," said one expert. "With over one in four people describing themselves either as an ostrich burying their head in the sand, careless as a bull in a china shop, or a possum paralysed with fear."
Up to 80% of successful data breaches, according to Verizon's annual Data Breach Index Report, are caused by stolen login information. However, the study found that 57% of respondents said they "watch their passwords like a hawk" or that they "take charge confidently" like lions. The fact that 40% of the former group didn't know if their passwords had been compromised suggests that many of those polled are either grossly exaggerating their level of computer literacy or wilfully disobeying password hygiene recommendations. Only 7% of respondents worldwide said that using password managers was the best way to ensure personal cybersecurity.
According to Craig Lurey, CTO and co-founder of Keeper Security, "Password management does not need to be complex, overwhelming, or difficult to understand even with a large number of digital accounts to secure." Anybody can protect themselves in the best way possible by using a password manager. A password manager can protect you against phishing attacks and malicious links in addition to generating and storing strong passwords for all of your online accounts. This is because it won't fill in the user's credentials if the URL doesn't match what's in their vault. Additionally, users can combine a password manager with dark web monitoring to keep track of all account information and respond swiftly in the event that credentials are stolen.
Other significant statistics in the report include:
30% of people still use simple passwords to protect their digital accounts, while 34% admit to repeating variations of the same password.
39% of respondents are unaware of whether they’ve been breached and 32% do not know whether their passwords are available on the dark web.
64% of respondents are not confident that they are managing their passwords well.
41% of respondents said cybersecurity is too difficult to understand.
29% of Baby Boomers use strong and unique passwords for every account, compared to only 20% of Gen Z respondents, of which 40% found cybersecurity overwhelming - highest of all the age groups.
Men are more confident than women about password security – 39% of men vs 31% of women.
On the other hand, Radware stops a DDoS attack that lasted seven days and 20 attack waves and had the size of a tsunami.
Shira Sagiv, vice president of products portfolio at Radware, recently revealed that the cyber security industry is in disarray.
Layer 7 (L7) HTTPS Flood attacks, also known as Web DDoS Tsunami attacks, are a new breed of aggressive attacks that bypass organisations' conventional DDoS protection and web application firewall (WAF) solutions to cause market disruption.
The destructive attacks, according to Shira, are designed to wear down an organization's security team. They come in multiple waves, last for days, and hit with extremely high volumes. Additionally, they pretend to be legitimate traffic, making it very challenging to identify and stop them.
Recently, Radware engaged in one of these attacks to protect a client and important international company. The ransom demand was the beginning of the attack, which progressed daily with new attacks and demands.
This is what was encountered:
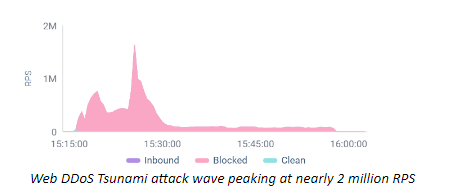
Ultra-high volumes: Some attack waves peaked at nearly two million requests per second (RPS).
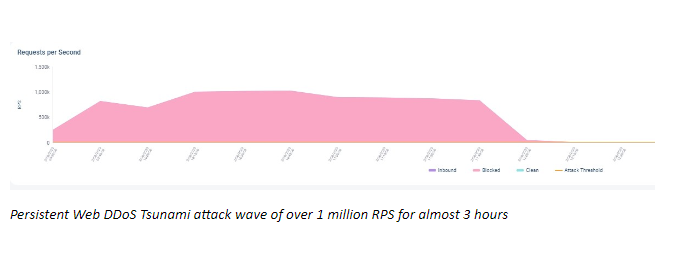
Persistent and long attacks: Over the course of seven days, we observed nearly 20 different waves. Some lasted several hours, reaching over 10 billion requests in aggregate.
Complex attacks: They were encrypted and crafted as HTTPS GET requests, posing as legitimate web requests.
RPS-heavy attacks often make headlines. The dangerous combination of volume, duration, and complexity distinguishes this new attack and recent attack campaign.
Hackers are combining network and application layer attacks with new tools to create L7 DDoS Tsunamis in their latest campaigns. Attacks use HTTP headers, cookies, IP spoofing, and more to avoid detection.
Rate-limiting solutions are not enough to defend against this combination over time. Traditional mitigation tools based on signatures or rate-based detections cannot stop these attacks.
Network-based DDoS protection cannot detect and mitigate L7 attacks.Scale and randomisation overwhelm standard on-prem or cloud-based WAFs. Rate-limiting harms legitimate traffic.
Thus, companies are surprised. Standard protections are overwhelmed and outmanoeuvred without a behavioural-based approach and automated real-time signatures, leaving businesses vulnerable.
Companies must rethink mitigation solutions to defend against this new DDoS generation. Organisations must use defensive automation to stop automated cyberattacks.
This includes behavioural-based algorithms that can automatically detect and quickly generate new signatures for unknown malicious requests at scale, in real time, and without false positives or blocking legitimate traffic.
The solution's service and support are important, especially since many security teams are lean.
The Web DDoS Tsunami is a new level of sophisticated attacks and emboldened actors in the DDoS attack evolution.
Before you go..
You can get RedWires AU for free right now. Your donation, no matter how big or small, will help us keep doing honest journalism.
The readers of Redwires AU are the engine that drives our publication. Add your support to the effort to create a sustainable future for journalism that does not make compromises in the AU.
In the world we live in now, accurate and thorough reporting and analysis are becoming more and more important. To stop the spread of false information, it's very important that everyone in Australia has access to good reporting.
The Redwires AU contributes to society by opening up access to information and resources for all people, rather than just a select few.
Our only goal is to educate the general public more thoroughly. If you believe in what we're trying to accomplish here, please consider making a contribution right away to ensure our success in the years to come.
Upgrade your subscription to get the most out of it. Join the growing number of people around the world who believe in the power of independent media.